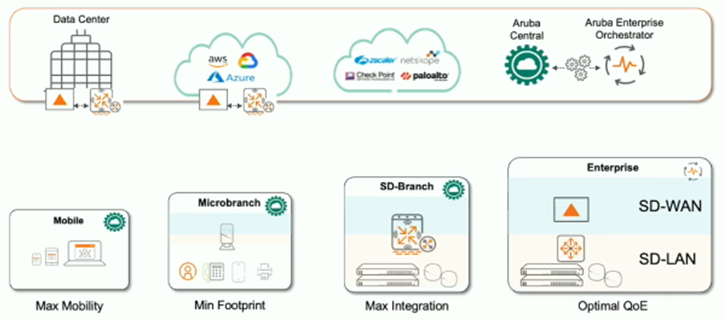
- EdgeConnect Mobile - VIA for remote VPN users
- EdgeConnect Microbranch - RAP/IAP for SOHO users
- EdgeConnect SD-Branch - "Office in a Box" style use cases
- EdgeConnect Enterprise - large office, enterprise use cases



|
Engaging customers via their mobile devices is an exciting proposition for many organizations; however, it has to be done with care. These solutions often carry a significant cost and depend on a Return on Investment (ROI) model to make sense.
Achieving this ROI requires walking a fine line between meaningful engagement and being a nuisance. Here are five best practices to help you do that.
|  |
5 ways to ensure your mobile strategy works1. Think big pictureThe goal is to create a user experience that provides vast amounts of data to the organization while delivering value to the customer. Accomplishing that means the experience needs to be immersive and omni-channel (e.g., SMS, email, app-based, digital signage, direct mail, etc.).
Too many organizations jump straight to the mobile application without realizing adoption of mobile applications is low and retention of those mobile apps is even lower. A holistic approach that embraces the web (traditional and mobile), mobile apps, digital and physical signage, and some of the emerging areas such as augmented reality (AR) and context-aware chatbots will be far more successful.
Analytics and business intelligence tools must be included because understanding the success of these messages and their impact on the bottom line is a necessity, as engagement attempts that are ill-received may create a negative effect on the business.
2. Establish a baseline
Before rolling out any new engagement solution or even a single targeted campaign, it is important to understand the baseline. What is normal for a specific time of day, day of week, demographic, location, etc.
If there are areas in which these baselines are unknown, the success of an engagement will also likely be unknown. The length of time to determine a credible baseline depends on business and vertical; however, a month of data will provide statistically valuable data for many organizations.
3. Consider your social credibilityEach engagement or touchpoint with the user must be carefully weighed prior to being implemented, as the organization is spending “social credibility" with the customer in issuing these engagements. Determining that a message is hitting the right person at the right time and place is paramount to success.
While the organization may want to drive a specific behavior, it must be done in such a way that it is graciously accepted by the recipient. For less important messages, consider other channels for delivery—email, direct mail and digital signage integrations are options that are less invasive than a targeted push message.
4. Leverage employee engagementBusiness should ensure the human component isn’t lost in this digital marketing frenzy.
Consider a scenario in which an employee could be notified when a user has spent more than five minutes in front of a specific retail display or there has been a high density of users in line for a drink at a sports game or concert venue. Rather than trying to ping users to have them go find another bar, consider triggers that have an employee come over with a mobile payment system and perform line-breaking transactions. This human component may still be considered a “digital engagement," but it won’t feel like it to the consumer.
5. Keep it freshDigital engagements should always be timely and relevant. Organizations can’t afford to be lazy about managing these platforms because pushing irrelevant messages will drive away customers, cause them to remove their mobile apps, and even consider competitors.
Campaigns should also create a sense of urgency—create a fear of missing out or at least ensure customers understand this immediate deal is good for only the first 100 redemptions.
Gamification is one way to keep things interesting for consumers, and it can drive additional spend as it may promise “bonus" rewards for the additional engagement. The solutions should be simple enough that they can be managed by marketing teams and not IT.
Originally posted here with Network World. Republished with permission as originating author. Also available on my LinkedIn page.
|





Frame Type | High-Order 4 Bits | Low-Order 4 Bits
(Reserved for Future Use) | Byte Value |
Unique Identifier (UID) | 0000 | 0000 | 0x00 |
Uniform Resource Locator (URL) | 0001 | 0000 | 0x10 |
Telemetry Data (TLM) | 0002 | 0000 | 0x20 |
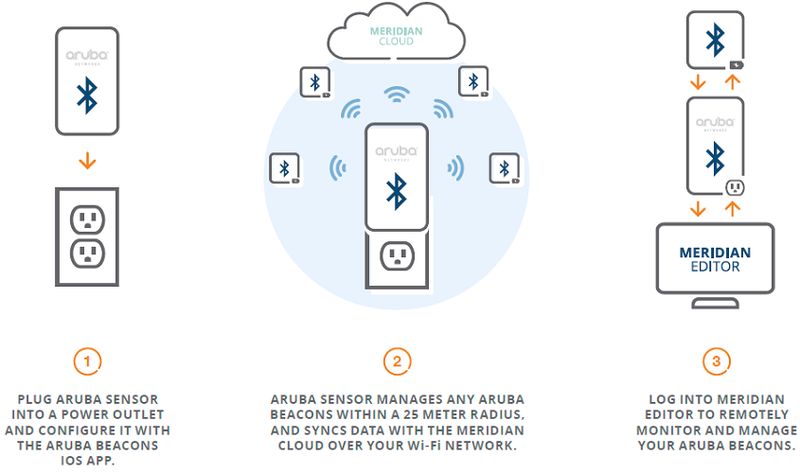
I opted for the BKON Eddystones to try, there are a few options out there, but I liked the approach and packaging that I saw on the BKON site and acquired them through Amazon (2 for $60). AAA batteries were included and already installed. Also included a screwdriver and 3M dual-sided sticky tape. One thing I am not a fan of is the lack of screw type mounts as seen on the Aruba beacons. I'm not convinced the 3M sticky tape will hold up as long as a battery will, especially for beacons in tougher climates--outdoors, fridge/freezer, high humidity, etc. That being said though, the overall packaging and included items are great!
PHY.Net
Setting up with PHY.net was painless, simple field with beacon ID (located on side of beacon), valid email address and contact info. BKON sends a validation email to confirm.
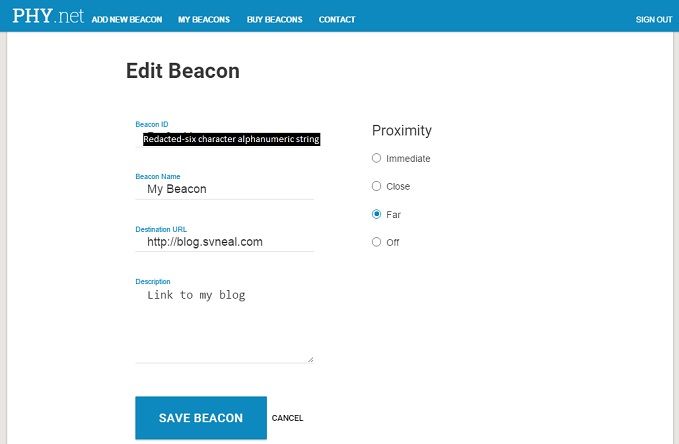 Browsing...and a surprise
As of right now a specific browser is needed to browse the Physical Web. The screenshot to the right is from BKON's own "BeaconPages" available for IOS. Alternatively, you can install "Physical Web" available on both IOS and Android. I found it interesting that this Physical Web app picked up my HP printer via Bluetooth and let me view the configuration page. Interestingly, the Bluetooth radio is configured as "off" on the HP printer. I could pull my MAC and IP addresses, subnet mask, gateway, DNS info and host names via the Physical Web browser. I would have to log in to the printer to change any settings, but I was still surprised at how much information was readily available. Perhaps the next blog post will be on security.....
|   |